Ransomware - What, How and Tips To Protect Against It
In recent years, the usage of computers and smartphones is on the rise and this massive growth opened the door for hackers. To gain such burgeoning market, hackers generally target innocent users with a wide range of malware. The main object of such threats is to earn money directly or indirectly from the victims. Today, we are going to discuss about Ransomware malware that is emerging threat at present and categorized as a troublesome malware.

Image Credit: Pixabay
What is Ransomware?
Ransomware is a type of malware that gains control of users PC, locks user system, gain access of files on the computer and demands for money to decrypt or unlock files. By taking advantage of open security vulnerability, it generally penetrates PC. There are most cases where ransomware attacks happened due to email click fraud and drive by downloads.
Let’s know about main types of Ransomware.
Types of Ransomware:
There are two types of ransomware: Locker and Crypto.
Locker Ransomware controls access to the user computer or device by locking it and ask for money to restore the device in original stage. Such ransomware limits the use of mouse and allows operating specified key strokes in keyboard like numeric keys. Compare to Crypto, Locker ransomware can be removed with various tools to restore the device at its earlier stage. Internet of things and wearable devices are more prone to such type of ransomware.
Crypto ransomware finds valuable data, encode it and make it useless unless the victim gets decryption keys. Crypto ransomware is more severe than Locker and has vast ground as most people store their valuable data on devices and personal computers. Until such malware finds the files, it remains undetected and silent on the system. Computer system can do regular activities apart from accessing the data held by hackers. In that case, strong and timely data backup is necessary to avoid such fuss.
How Ransomware works?
Mostly ransomware spread through phishing email, drive by downloads, traffic distribution system, malvertisement, social engineering, fake update. Once the user clicks on such links or open malicious attachment, ransomware enters into the user’s device system and tries to search for security vulnerabilities. After finding vulnerability, it carries out digital extortion which is a planned activity designed by cyber crooks. When ransomware infects the user computer, it blocks data access and convince a user to pay the ransom to gain access to the data. It is seen that cyber crooks demands Bitcoin to restore the data in its earlier stage.
What Research Says?
According to McAfee Threat research, there is seen a 165% spike in ransomware target in first quarter of 2015 year. There are new breeding of ransomware family emerged like CTB-Locker, along with new versions of CryptoWall, TorrentLocker, and spikes of BandarChor.
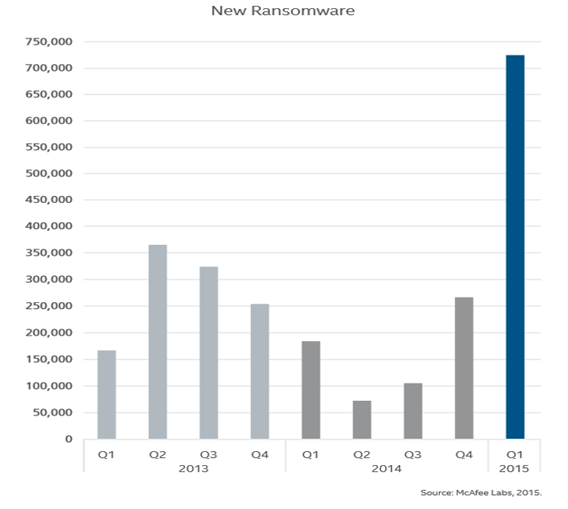
Cyber criminals target rich countries, as people in such countries are willing to pay the amount to get back their files and data. New technologies have been using by cyber criminals include virtual currency for payment, use of Tor Network, targeting android platform and network attached storage.
Steps to protect against Ransomware:
Regular back-up
If you backup regularly either on external hard disk or online backup service, you do not have to worry about ransomware. Just turn off the computer and start with reinstall it. It is essential to restore the system after six months to clean off threats in the system. While backing up your data, do not overwrite the new data with compromised data as it may cause trouble at the time of restoration.
Employ security
A security approach should be considered while mitigating ransomware. Ensure that you have defenses like antivirus, firewalls, web traffic filtering, pop up blocker tools etc. Even make user policy that can restrict app data or local data from where attackers run executables.
Update software
Software vulnerability is a main concern in current times, many enterprises do lack of software patches that can attract attackers. Ransomware always find loopholes in software and gain access of the files or folders. Installing patched timely can avoid different threats targeting to your computer system.
Exclusive rights of users
It is essential to keep watch over user activity hence users should give restricted right. Once the person with global administrative rights is compromised, cyber crooks can access the same resources and can access data resides on network drives and removable media.
Dealing with criminals
There is no guarantee that after receiving ransom, cyber crooks will release the data or files so it is better to understand the level of sophistication and sensitivity of data applied in ransomware attack. Once you pay ransom, you may be an easy and potential target of cyber crooks.
Disconnect the Internet
If you have, data back up and under the ransomware attack, then disconnect your computer from the internet as your sensitive data could be transmitted back to criminals. Just shut down the computer and restart it. If the computer does not restart, take it to the service center.
Avoid false clicking
As ransomware can be spread via phishing email, fake sites, or malicious downloads, it is wise to keep away from clicking malicious emails or links. Before responding to emails or sites, check the authenticity of the website.
Conclusion:
As the ransomware rises timely, it is sensible to take precaution steps against ransomware. There are chances that new variants and families of this threat will appear so staying aware allows us to detect and stop most ransomware before it can execute.


