Secure Sockets Layer - A Process Of Secure Communication
We know that SSL encrypts the information and protect user information in an encrypted form over the internet. After getting an overview of SSL certificate, certificate authority, and importance of SSL, in this article, we will know about SSL protocols, which define the whole SSL process.
SSL Protocols:
An SSL Certificate sets up a confidential communication channel between the browser and web server empowering encryption to the data during the transition. SSL certificate contains two keys: a public key that is used to encrypt the information while the other private key is used to decrypt the information. Generally, SSL protocol works on four main layers, which comprises SSL Record Layer, SSL Change Cipher Spec, SSL Alert Protocol and SSL Handshake protocol. Let's have look at SSL Protocols:
1. SSL Record Layer Protocol
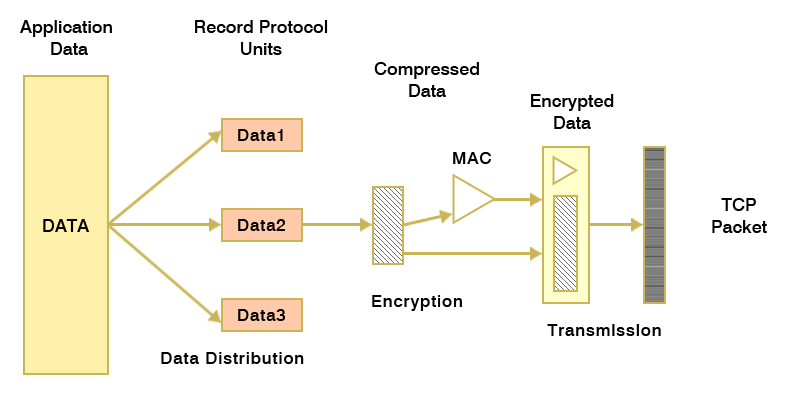
The SSL record protocol ensures about message integrity. The purpose of the SSL record protocol is to transmit the application message; split up the data needs to be sent, encapsulate the data with suitable headers and create an object called the record, which is encrypted. The record sends data to the TCP protocol. The transmitting data involves a process like
- The data is fragmented into 16kb fragmented size and further it may be compressed. However, SSL 3.0 contains no compression protocol.
- The creation of Record layer is required for each data piece along with a header, information to complete the data size and the MAC (Message Authentication Code). The header includes the length of the record and the length of the data block.
- The next step is to add primary data, information to complete the datagram and MAC value. Here, MAC is for the confirmation of message integrity contained in the transmitted record, and MAC is the result of hash functions that follows an exact hash algorithm for instance MD5 or SHA-1. It requires a secret key in creation of MAC, which can be of client side or server side. After getting the packet, the receiver party calculates the obtained MAC value against its own value and if two values are same then it is a sign that the data is not altered during the transition.
After the above steps, a specific symmetric encryption algorithm (DES) encrypts the data and MAC. The prepared data include the following header fields:
- Content type: Types of payload delivered by the packet will decide the type of higher protocol to be used for data processing. The possible value referred to proper protocols is Change Cipher spec, alert, handshake and application data.
- Major Version: It contains setting up of the main part of the protocol version to be applied. For SSL 3.0, the value will be “3”.
- Minor Version: It contains setting up the additional part of the used protocol version. For SSL 3.0, the value will be zero.
After the above field addition, the procedure of record preparation is now finished after filling all the required fields and the record will be transmitted to the addressed point.
2. SSL Change Cipher Spec
The Change Cipher Spec Protocol is made of a single message and that message carries length of a single byte. The Change Cipher Spec Protocol reveals about a sign of a beginning of a secure communication between the client and the server. This protocol fixes the pending data session and it carries a value of “1”. After the exchange of the message, the session is believed as accepted. All the messages use SSL record protocol for the transition.
3. SSL Alert Protocol
The Alert protocol is used to transmit session messages correlated with data exchange and data protocol. This protocol indicates about any errors, warnings in the connection between two parties. This protocol divides into two parts: Severity level and Alert description.
- The severity Level: The severity level sends two messages with a value of “1” and”2”. If it sends a value “1”, it shows that the client has disconnected the session and tries to use a new handshake while the value “2” shows a fatal alert message and indicates about discontinuance of a session.
- The Alert Description: It shows a specific error sends by a respondent. The error message can be labeled as CloseNotify, Unexpected Message, BadRecordMAC, Decompression Failure, Handshake Failure, No Certificate, Bad Certificate, Unsupported Certificate, Certificate Revoked, Certificate Expired, Certificate Unknown, and Illegal Parameter.
4. SSL Handshake Protocol
The communication between the server and the client establishes a secure connection called Handshake. To perform a handshake the following steps have to be followed.
- Client Hello: Initially a connection is established between a client and the server in which the client sends a Client Hello to the server, and contains the data like SSL version no., cipher suite supported by the client, compression methods, and besides there are two types of other information include in this message like Session ID and 32-byte random number. The 32-byte random number helps the client to establish a secure connection while Session ID field remains blank.
- Server Hello: The second message is ServerHello and it is a response to a ClientHello message with returning five fields, which includes an SSL version number (Highest version number), a compression algorithm, strong CipherSuite, the new session ID or resumes with same ID indicated in the Client Hello, and 32-byte random value (where 4-byte for server date and time stamp and the rest 28-byte is for using with the client random value).
- Server Key Exchange: This is an optional step in which the server produces and sends a temporary key to the client. The client can utilize this key to encrypt the Client Key Exchange message. The part of the server key exchange is only expected when the public key algorithm does not offer the key to encrypt the Client Key Exchange message.
- Server Hello Done: After completing the server key exchange, the client obtains a server HelloDone message indicating a completion of task of server side and waiting for the response from the client.
- Client Key Exchange: The Client Key Exchange message holds details about the key that the client and server will utilize to communicate. After calculating the premaster secret with both random values (encrypted with the public key from the server certificate), the client sends key exchange message. If the server is successful to decrypt the data, then the client will be assured about the server authenticity. Only the server has the private key that matches with the certificate’s public key can decrypt the message. This message finishes the dialogue processes between the client and the server.
- Change Cipher Spec: This message informs and assures the server that the keys and algorithms will encode all messages that are identified as a valid Finished message from the client. It indicates about the data transformation from the insecure status to a secure state.
- Finished: The final message is a hash of the entire exchange of session keys and MAC, which verifies the three things: key details, content of previous SSL handshake messages, and a special value indicating the identity of the client and the server. At the end of the process, the client will see a padlock indicating a secure protocol in the corner side of the browser.
Conclusion:
The SSL process requires a diligent effort, based on authenticity and reliability, which sets it apart from other security solutions. Above four SSL protocols play a vital role in establishing a secure and authenticate connection between the server and the client. Besides authenticity and reliability, ssl encryption integrity is also important in the whole ssl process.


